Technology
Data Stewardship Frameworks: Defining Roles and Responsibilities for Corporate Governance
Introduction Strong corporate governance increasingly depends on how well an organisation manages data. In many companies, data is created across departments, stored in multiple systems,…
Master Data Management: The Backbone of Reliable and Scalable Data Governance
Imagine an organisation as a vast library, with thousands of books constantly being borrowed, returned, updated, or rewritten. In such a setting, chaos would erupt…
Transform Coding: Mapping Data to a Different Domain to Concentrate Energy Before Quantisation
Imagine an artist painting a vast mural. Before starting, she sketches a small outline to decide how to place every colour and shape efficiently. In…
HGX B200 vs Alternative GPU Architectures — Performance, Memory & Use-Case Comparison
Choosing the right GPU platform is a strategic decision for AI teams. NVIDIA’s HGX B200 (Blackwell) represents the latest scale-up approach, while previous generations (H200/H100) and…
SAFe vs PMP: Which Certification Should You Choose in 2025?
In today’s fast-paced project management world, professionals are constantly looking for certifications that can sharpen their leadership skills and improve career opportunities. Two of the…
Internet
Some examples of cold emailing and why they work?
What is the most important goal of cold emailing? To ensure that your email is read. So, what should the primary purpose of your opening…
Using Internet Fax to Increase Efficiency and Profits in Your Construction Business
The construction market is very susceptible to the laws of supply and demand, and in an economic slump, construction contractors are often hit hard. In…
Internet Identity Theft and How to Prevent It
The traumas and problems associated with identity theft are by no means new on the scene. Those of you who are accustomed to working on…
Want Cheap Satellite Internet – Here’s How
Compared to other types of high speed internet, satellite internet is more expensive. But if you can’t get cable or DSL where you live, a…
Social Media
Comprar Seguidores por 1 Real Fortalece a Construção da Sua Marca
No universo digital competitivo de hoje, a construção de autoridade, reputação e presença de marca se tornou o grande objetivo de profissionais e empresas de…
Like Pump supports content visibility with increased engagement.
Content creators and businesses alike are constantly seeking ways to stand out in the crowded digital landscape. The struggle for visibility and meaningful engagement persists,…
Comprar Seguidores por 1 Real: Entenda Por Que Vale a Pena no InstaBarato
No mundo digital atual, especialmente no Instagram, a presença online é um dos principais indicadores de sucesso, seja para influenciadores, empresas ou marcas pessoais. Uma…
Como Comprar Seguidores Baratos com Segurança no InstaBarato
Se você está procurando maneiras de aumentar seu número de comprar seguidores por 1 real no Instagram rapidamente e sem gastar muito, você veio ao…
Electronics
Discount Marine Electronics GPS Software – Garmin BlueChart G2 Series
Confused about the complex array of marine navigation software for your Garmin Marine GPS? You are not alone. Here we will take a look at…
Electronic Watchdog – The Best Value in a Simple Wireless Home Security Device
In case you haven’t been watching home security has turned out to be an absolutely huge business. You can spend as much money as you…
How to Simplify Your Electronics
Many people get too many electronic devices. Old ones are replaced with newer models. There are cords and accessories to these devices all over the…
Your Dog’s First Command and the Correct Use of Electronic Collars – First of a Two Part Series
You can use this method in teaching your dog to understand and obey numerous other commands. Before giving the command like to call the dog’s…
Application
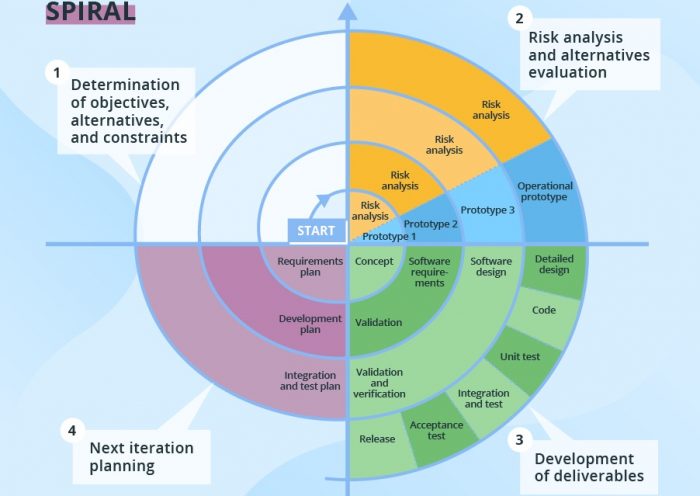
Importance and Working of Best Rapid Application Development Models
Most firms are already in the initial stages and are only beginning to see the advantages of this reduced RAD paradigm and its ability to…
How to Promote Your Blog Posts with Facebook Messenger Ads Through Steps
So, the most important question which has been in your mind for long and disturbing you a lot is How to Promote Your Blog Posts…
Tiger Text – If Only Tiger Woods Had This Cell Phone Application
How Does Tiger Text work? Tiger Text is basically a service that will handle all of your text messages. A software application that runs on…
Users Can Interact With Facebook Applications
Facebook applications are popular, and we’re confident that 9 out of 10 readers reading this would be regularly using at least some of the thousands…
Online Credit Card Application – How Safe is It?
There have been many speculations about the safety of cardholders when they purchase items online using their cards. However, only a few are discussing about…